Access you can trust: Identity and access management for enterprise content operations
Published on January 26, 2026

In a recent deep dive on audit logging, we focused on one side of platform trust: maintaining a clear, reliable record of what happens across your content operations. This post looks at the other side, who is allowed to do what, and how enterprises keep those permissions aligned with their security posture as organizations grow.
Over the past few months, we’ve made targeted improvements to Contentful’s identity and access management (IAM). Together, they close common security gaps without slowing the teams who create, manage, and ship content every day. These updates focus on tightening controls around SSO exceptions, improving visibility into security posture, governing personal access tokens more effectively, and introducing finer-grained access at the environment level.
Below is a practical look at what’s changed and how these capabilities work with audit logs to strengthen trust across enterprise-scale content operations.
Why IAM matters more at enterprise scale
Contentful often sits at the center of a broader composable architecture. Websites, mobile apps, personalization engines, commerce platforms, and internal tools all depend on shared content. On any given day, marketers, engineers, product teams, agencies, and automated systems may be working in parallel across the same organization.
In this environment, speed matters, but so does control. Security and compliance teams need confidence that access is tightly governed and easy to demonstrate during audits. Platform and digital experience leaders need assurance that permissions reflect how teams work today, not how tools were configured years ago.
Audit logs help you reconstruct what happened when something looks off. IAM determines who could have taken that action in the first place, and how quickly you can reduce risk when conditions change. That’s why recent IAM work has focused on strengthening fundamentals while keeping everyday workflows fast and familiar.
How IAM works in Contentful today
At a high level, IAM in Contentful is built on three core capabilities.
Authentication defines how users sign in and how sessions are secured. This includes single sign-on (SSO) through your identity provider, session controls, and multi-factor authentication (MFA), also known as two-factor authentication (2FA).
Authorization governs what authenticated users and systems are allowed to do. It spans organization and space-level roles, content permissions, and granular controls at the environment-level.
Token management covers non-human access. Personal access tokens (PATs) and management tokens are used by scripts, integrations, and automations, and they require the same discipline as user access.
These building blocks have existed for some time. The latest improvements strengthen how they’re applied in enterprise scenarios, particularly in areas that tend to surface during security reviews and audits.
Recent IAM improvements, explained
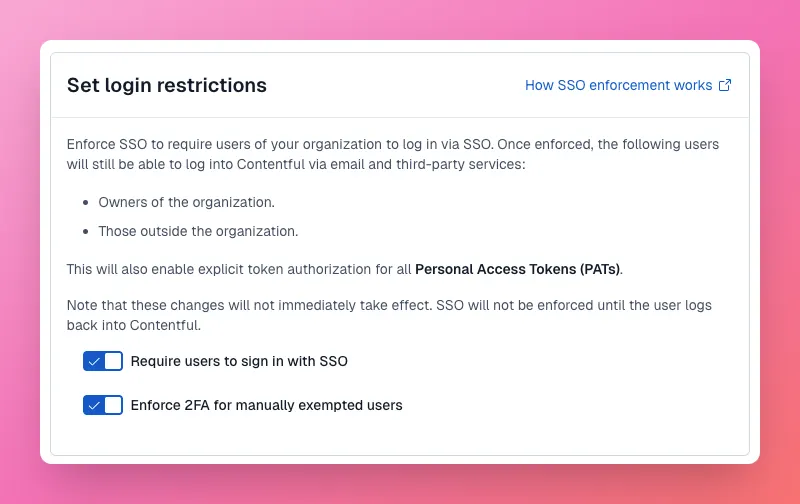
1. Raising the threshold for SSO-exempt users
SSO enforcement allows organizations to require users to authenticate through their identity provider instead of email or social logins. Historically, organization owners were automatically exempt, creating an avoidable blind spot for some enterprise teams.
Today, organization owners in new organizations are subject to SSO enforcement by default. Administrators can still explicitly mark certain accounts as SSO-exempt, for example, a designated break-glass account, but those exemptions are now intentional and visible.
To reduce residual risk, SSO-exempt accounts can be held to a higher standard through MFA. The sec-check command in the Contentful CLI flags any SSO-exempt users who do not have MFA enabled, giving teams a clear, actionable list to resolve.
The outcome is a smaller, well-defined set of exceptions paired with stronger safeguards and better visibility. Read more about two-factor authentication for SSO-exempt users.
2. See security posture from the command line
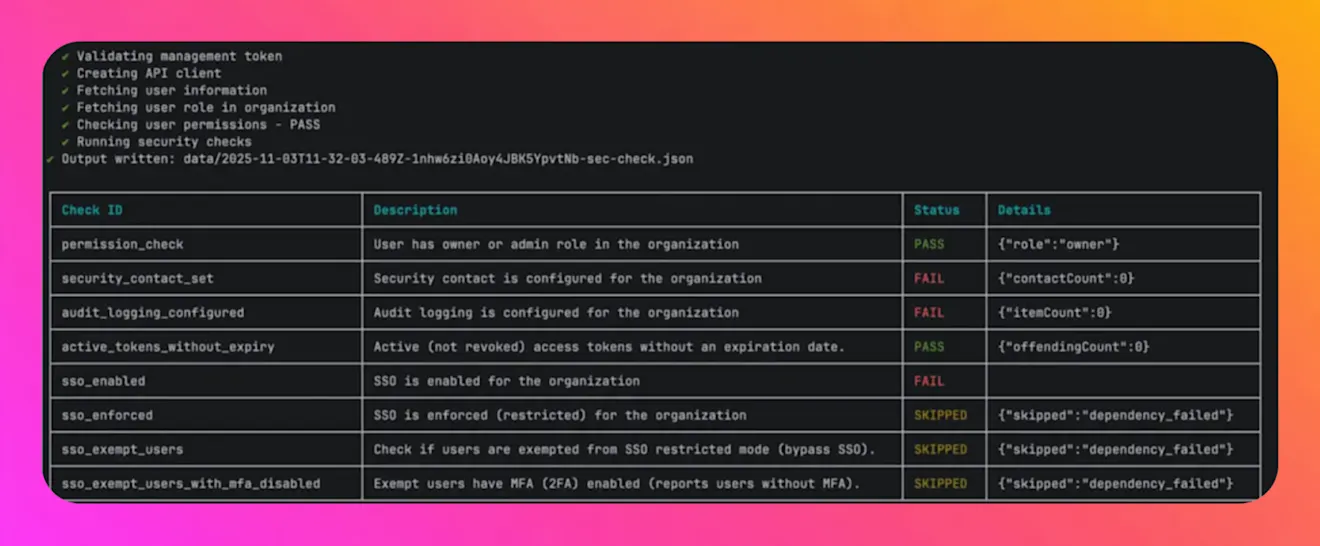
Security reviews often happen far from the tools where configuration changes are made. The sec-check command brings key IAM and security signals closer to daily workflows.
From the CLI, teams can quickly confirm whether a security contact is configured, audit logging is enabled, SSO is enforced, and whether any SSO-exempt users lack MFA. The command also highlights personal access tokens with unusually long expiration periods.
Each check returns a simple pass or fail result with enough context to act. Results can be exported as JSON and fed into dashboards, ticketing systems, or continuous integration pipelines. Many customers use this as a lightweight health check before launches or audits, or to catch security drift as part of CI/CD.
More about assessing your Contentful organization's security posture with CLI command.
3. Bring personal access tokens under tighter control
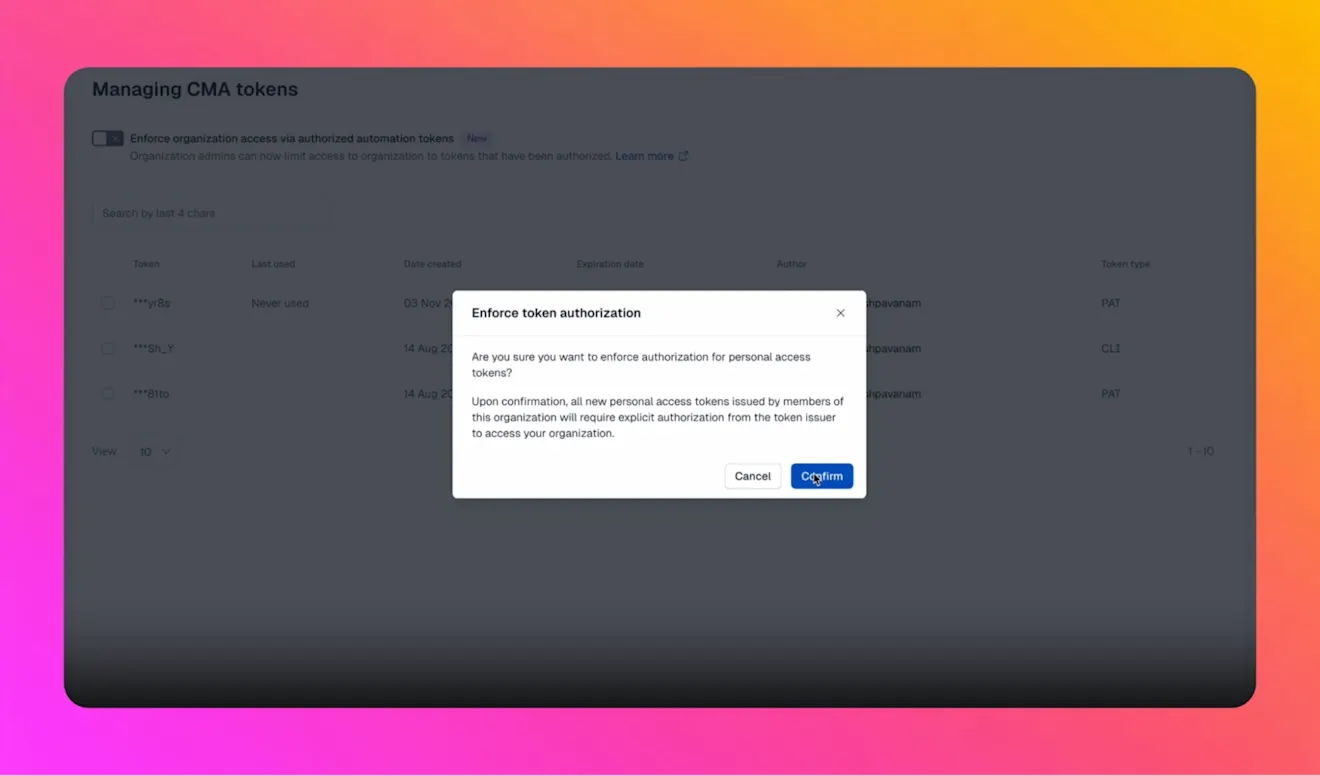
Personal access tokens are essential for automation and developer productivity, but they’re also a common source of risk when left unmanaged. Two related improvements help reduce that risk without disrupting existing workflows.
First, token authorization can be enforced at the organization level. When enabled, tokens created by a user are not automatically valid across every organization they belong to. Users must explicitly authorize a token for each organization, and administrators can deauthorize tokens locally without revoking them globally. This makes it easier to remove access when a project ends or a vendor relationship changes.
Second, token expiration and rotation are easier to adopt by default. When creating a new personal access token, users can set an expiration date. Tokens are automatically revoked when they expire, and reminder emails are sent as that date approaches. Combined with visibility from sec-check, long-lived credentials become the exception rather than the norm.
Read more about token authorization controls for organization admins.
4. Aligning access with environments, not just spaces
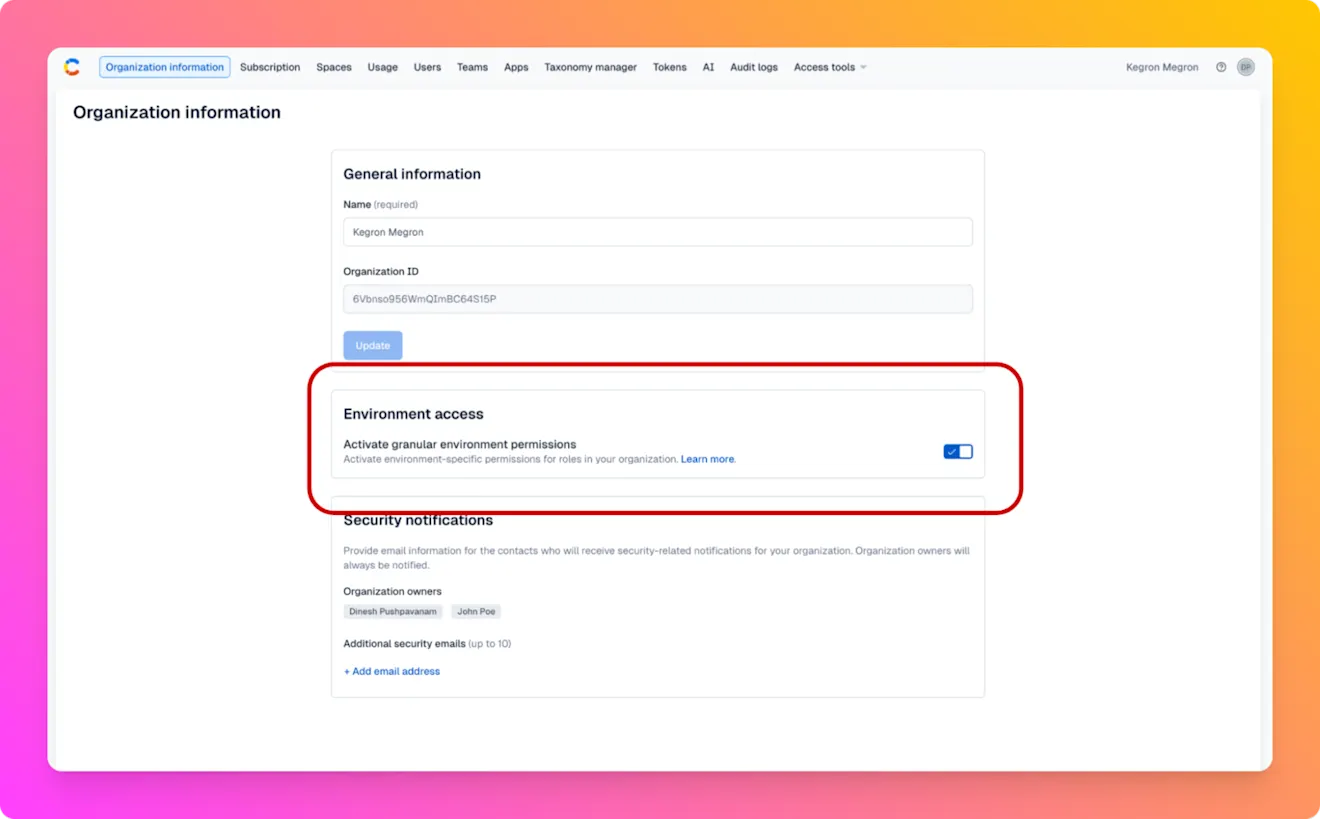
Spaces are often used to separate brands, products, or markets. Environments within a space represent stages such as production, staging, quality assurance, and sandbox setups. Until recently, access was primarily controlled at the space level.
Granular environment permissions make it easier to mirror real organizational structures. For each role, administrators can restrict access to the master environment only, select specific environments, or allow full access to manage and use all environments.
This supports common enterprise patterns. Content authors can work in production and a single staging environment. QA teams can access multiple non-production environments without touching production. Agencies can be limited to dedicated sandboxes. Teams share models and infrastructure without granting broad access everywhere. Read more about granular environment permissions.
Rolling out stronger IAM without slowing teams down
Because these improvements build on existing IAM capabilities, they can be introduced gradually. Many organizations start by running sec-check on a regular cadence to establish a baseline.
From there, SSO enforcement can be tightened, exemptions reduced and protected with MFA, and token authorization and expiration introduced over time. Environment permissions can be refined role by role so most users see only the environments they need to access.
Throughout this process, audit logs remain the detailed record of activity across users, tokens, and automation.
From guardrails to enterprise confidence
These IAM updates focus on fundamentals: clearer identities, scoped permissions, safer tokens, and a security posture that’s easy to inspect. Together, they make it easier to trust the platform as teams, brands, and regions scale.
Looking ahead, identity and access management in Contentful will continue to evolve to better reflect how large organizations operate. The aim is simpler access management, greater consistency at scale, and closer alignment with the identity systems and governance models enterprises already rely on.
Strong guardrails should reduce friction, not increase it. When identity and access reflect how the business is structured, digital teams can move quickly across spaces and environments, while security and platform leaders stay confident that access remains controlled, auditable, and ready for enterprise scrutiny.
If you’re evaluating how IAM fits into your broader governance and security strategy, your Contentful account team can help map these capabilities to your organization’s requirements and rollout plans.
Inspiration for your inbox
Subscribe and stay up-to-date on best practices for delivering modern digital experiences.






