- About Contentful
- APIs
- Backup, security and hosting
- Basics
- Best practices
- Billing
- Client libraries
- Content migrations
- Content operations
- Contentful AI functionality
- Environments
- EU data residency
- Extensibility
- Legacy spaces
- Managing organizations and spaces
- Personal access tokens
- Rich text
- Search and content organization
- Security and privacy
- Single sign-on (SSO)
- SSO x509 certificate expiration
- Technology and features
- Terminology
- Two-factor authentication (2FA)
- Versioning
- Web app
- Webhooks
FAQ / Single sign-on (SSO)
On this page
- How do I sign into Contentful with my corporate credentials?
- What Identity Providers (IdP) does Contentful support?
- Why do I get signed out of Contentful when using a single sign-on?
- How can I activate and deactivate SSO access for my organization?
- How do I set up a single sign-on access for my organization?
- How do I deprovision users?
- How are invited users affected by the use of a single sign-on?
- How does SSO Enforcement work?
- Is the single sign-on feature available for all customers?
How do I sign into Contentful with my corporate credentials?
If your organization has the single sign-on (SSO) option enabled, on the Login page click on the "Login via SSO" link at the bottom.
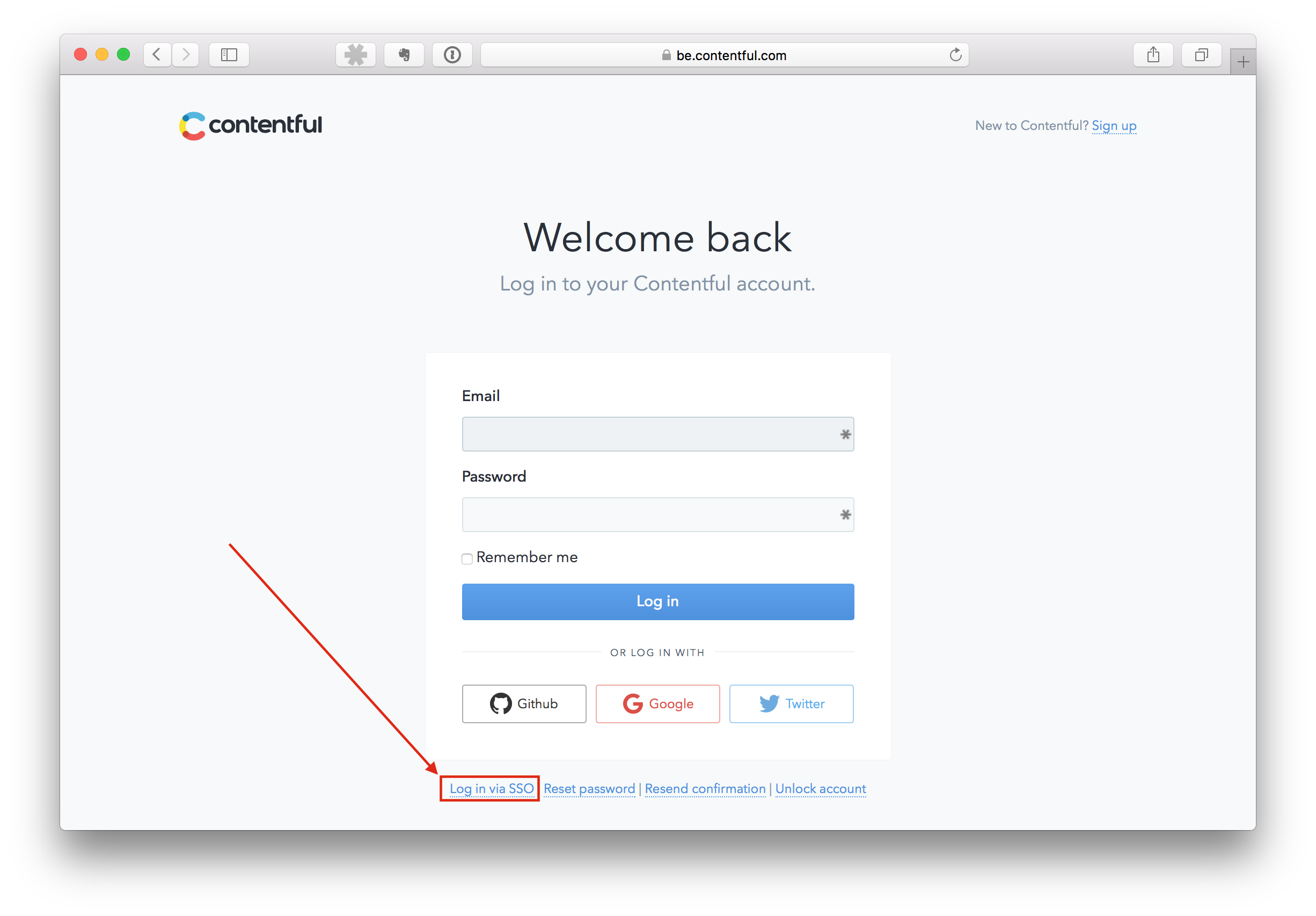
Next, provide the SSO name of your organization. If you are not sure about the name, contact your organization administrator.
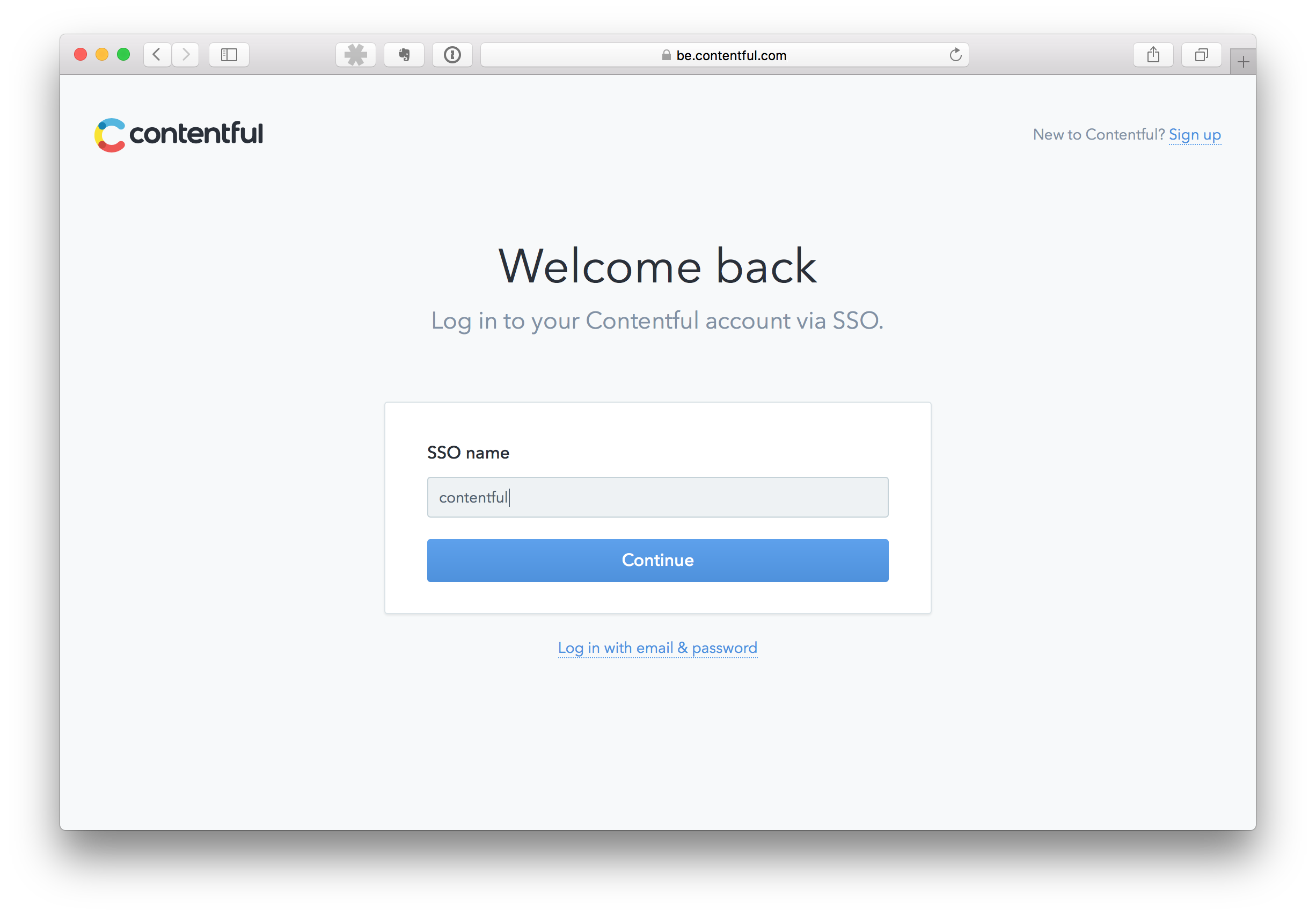
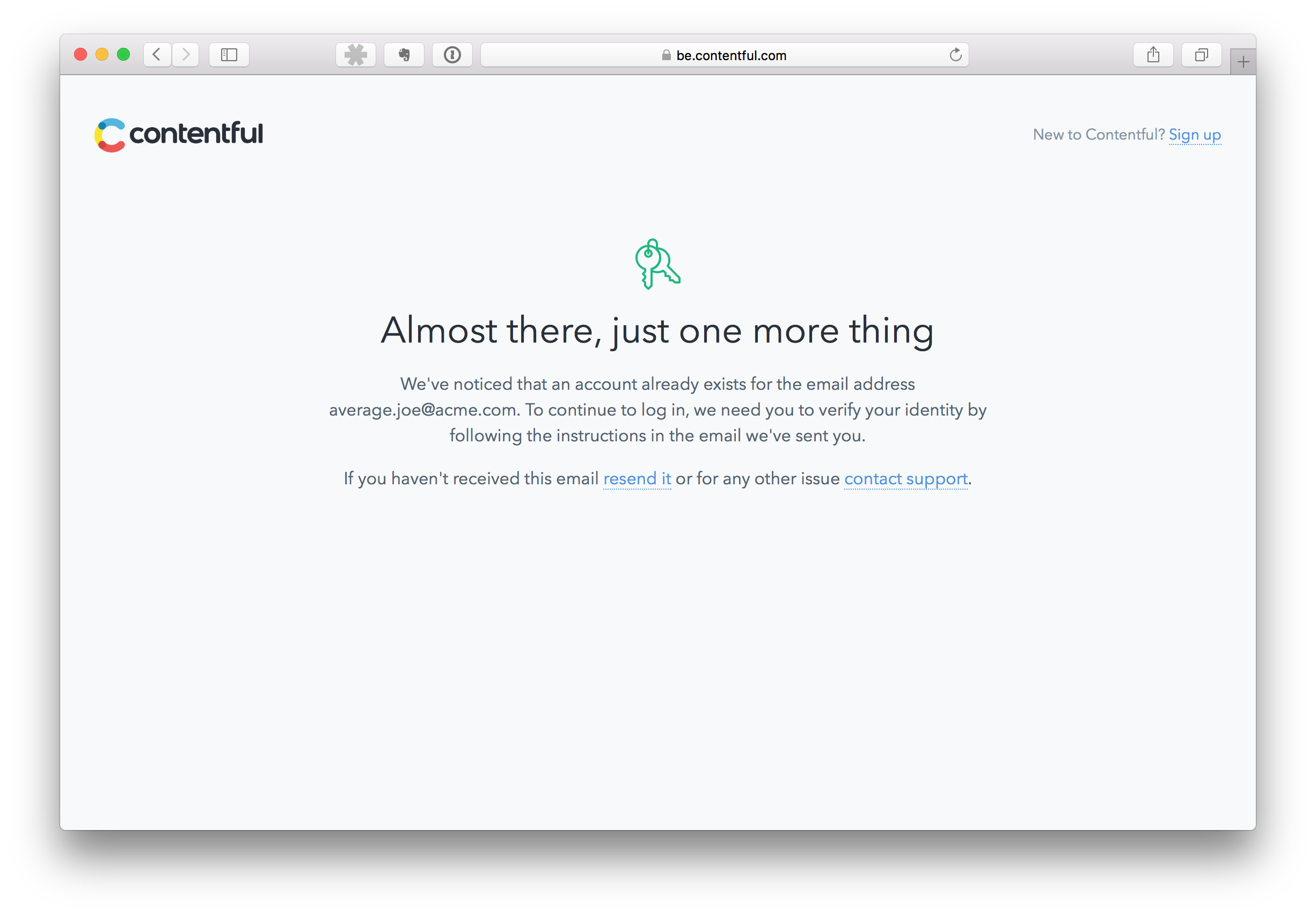
Login via your corporate Identity Provider. Note that if you already had a valid Contentful account, at this point, you will be prompted to confirm your email by clicking a link. This step helps to bind your existing Contentful account to the corporate account.
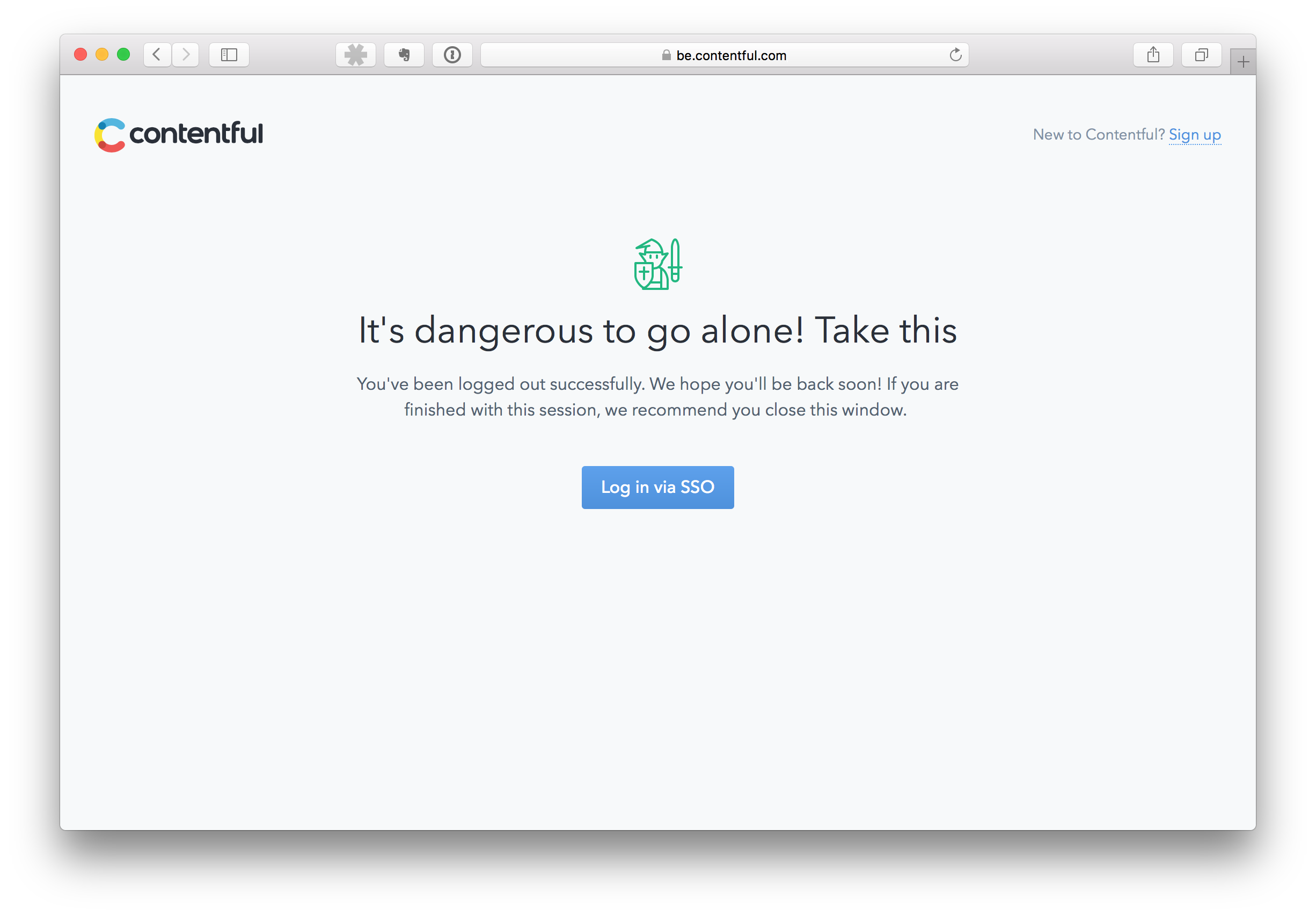
After completing these steps, you should be successfully logged into Contentful. When you sign out of Contentful, you will be redirected to a dedicated SSO logout page. Bookmark this page for one-click access to Contentful in the future.
What Identity Providers (IdP) does Contentful support?
Contentful SSO works with all Identity Providers that support the SAML 2.0 protocol, including Okta, Microsoft Azure AD, OneLogin, Ping Identity, Auth0 and G Suite.
Predefined integrations
Search for predefined Contentful SAML 2.0 integrations in these IdPs:
Microsoft Azure AD
miniOrange
Okta
OneLogin
Ping Identity
Why do I get signed out of Contentful when using a single sign-on?
For security purposes, users accessing Contentful via SSO are confined to sessions of a limited duration. The standard SSO session time is set at 12 hours, but the administrator at your organization can extend or shorten this period, provided your identity provider supports the sessionNotOnOrAfter parameter, according to internal needs and security policies. If your Identity Provider does not offer this feature, contact our customer support for assistance in configuring a custom SSO session duration.
How can I activate and deactivate SSO access for my organization?
To activate your SSO access to your organization, complete all required steps on the configuration page and click Save changes at the top right of the page. Once changes have been saved, click Activate SSO.
If your SSO access has been activated and you would like to deactivate SSO access for your organization, click Deactivate SSO at the top right of the page.
Deactivating SSO will allow users in your organization to log in without SSO. Once deactivated, users in your organization can log in using other methods, such as their email and third-party services.
For additional assistance, please contact Contentful customer support.
How do I set up a single sign-on access for my organization?
Your organization admin can request SSO within the web app. They will first need to select an SSO provider, as the provider name and details will be needed when setting SSO up within Contentful.
NOTE: You can leave the setup page and return to continue where you left off at any time by clicking Save changes at the top of the screen.
1. SSO name and confirmation
To initiate the setup process it is required to create your SSO name. The SSO name is a unique identifier for the organization to log in via Contentful’s SSO. The SSO name has to conform to the following requirements:
Composed in lowercase.
Includes the following symbols: 0-9, a-z, and =-_~\/
Contains no spaces.
A unique name across all Contentful organizations.
Confirm the enabling of SSO in the dialog box that follows to complete the SSO setup.
NOTE: If you would like to set up a SHA fingerprint of your certificate, contact our customer support.
2. Contentful Service Provider Configuration
Add the following details into your SSO provider:
Audience URI (also referred to as Entity ID, Issuer ID, or Identity Provider ID)
Assertion Consumer Service (ACS) URL (also referred to as SSO URL)
Map the user attributes required by Contentful with the corresponding user attributes in your Identity Provider. These attributes are named as follows:
Given Name: the givenname (or first name) of the user.
Surname: the surname (or last name) of the user.
Email: the email address of the user.
Fill in the form to provide us with details about your selected SSO provider, redirect URL, and X.509 certificate.
SSO Service URL: URL of the SSO endpoint specified by your Identity Provider, for example, https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=idpid
Signing certificate: a valid X.509 public signing certificate provided by your Identity Provider, used to sign SSO responses. Note that if you would like to set up an SHA fingerprint of your certificate, please contact Contentful customer support.
Many identity providers will also ask you to configure the Name ID attribute. Contentful uses this attribute to identify your users on subsequent SSO log-ins. As a result, the Name ID should be mapped to a field that uniquely identifies your individual users, such as email address, employee number, or a unique user ID made available by your Identity Provider.
NOTE: Most of the required technical details are included in the metadata file provided by your Identity Provider. Your organization’s SSO administrator should have access to this file.
3. Identity Provider Details
Once SSO is enabled on the Contentful side, your organization’s SSO admin will have to complete the setup process on the Identity Provider side as well as ensure that any other relevant settings on internal networks and applications are updated to allow employees access Contentful via SSO.
Many identity providers will also ask you to configure the Name ID attribute. Contentful uses this attribute to identify your users on subsequent SSO log-ins. As a result, the Name ID should be mapped to a field that uniquely identifies your individual users, such as email address, employee number, or a unique user ID made available by your Identity Provider.
NOTE: Most of the required technical details are included in the metadata file provided by your Identity Provider. Your organization’s SSO admin should have access to this file.
Test the connection
Once you have added the IdP details, you will need to test the connection by clicking Test Connection. By clicking on the button, you will be brought to the IDP login screen. After logging in, you will be returned to the setup page, which will now indicate the pass/fail status of setup
NOTE: You must re-test the connection if you want to apply a new X.509 certificate to your SSO configuration.
How do I deprovision users?
Deprovisioning a user on the IdP side will have an immediate effect of preventing the user from logging into Contentful. However, the user will still be listed as a member of the Contentful organization - and incur user fees - until they are manually removed by the organization admin.
NOTE: If your organization has not enabled SSO enforcement, users will be able to log in with their login credentials.
How are invited users affected by the use of a single sign-on?
When a user with pending invitations from multiple Contentful organizations accepts an invitation from the organization with Enforced SSO, all other invitations are purged and the user is uninvited from other organizations. If the user wishes to be a member of multiple organizations, they have to accept the invitation from the non-SSO organization first or be manually exempted from the SSO enforcement in the SSO-enabled organization.
How does SSO Enforcement work?
Enforcing SSO prevents organization members from logging into Contentful via email or third-party services (Github, Google, and Twitter). Once enabled, the only permitted authentication method for logging in will be through SSO.
Setting up SSO enforcement comes with two caveats. Enforcing SSO will require users of your organization to log in via SSO. Once enforced, the following users will still be able to log into Contentful via email or third-party services:
Those who have been explicitly exempted from SSO enforcement.
Users who remain logged into Contentful prior to enforcing SSO can continue using Contentful without SSO enforcement. Only after their current session expires will they be forced to log in via SSO.
NOTE: Enforcing SSO is an optional feature. You can choose to activate this feature by switching the toggle on or off located in the login restrictions section of the edit user page.
Is the single sign-on feature available for all customers?
The single sign-on feature (SSO) is available free of charge to all Premium customers. To enable SSO for your organization, navigate to the SSO configuration option under the “Access tools” tab in “Organization Settings & Subscriptions” and follow the guided setup process. This option is accessible by your organization admin.