Manage access to environments
Environments access levels
You can configure a role's access to environments under the "Environments" tab in the Role editor page. You can select a level of access to environments for your role according to the following options:
Master environment only (default) - Allows you to set your role to access only the master environment. The role won't be able to access non-master environments.
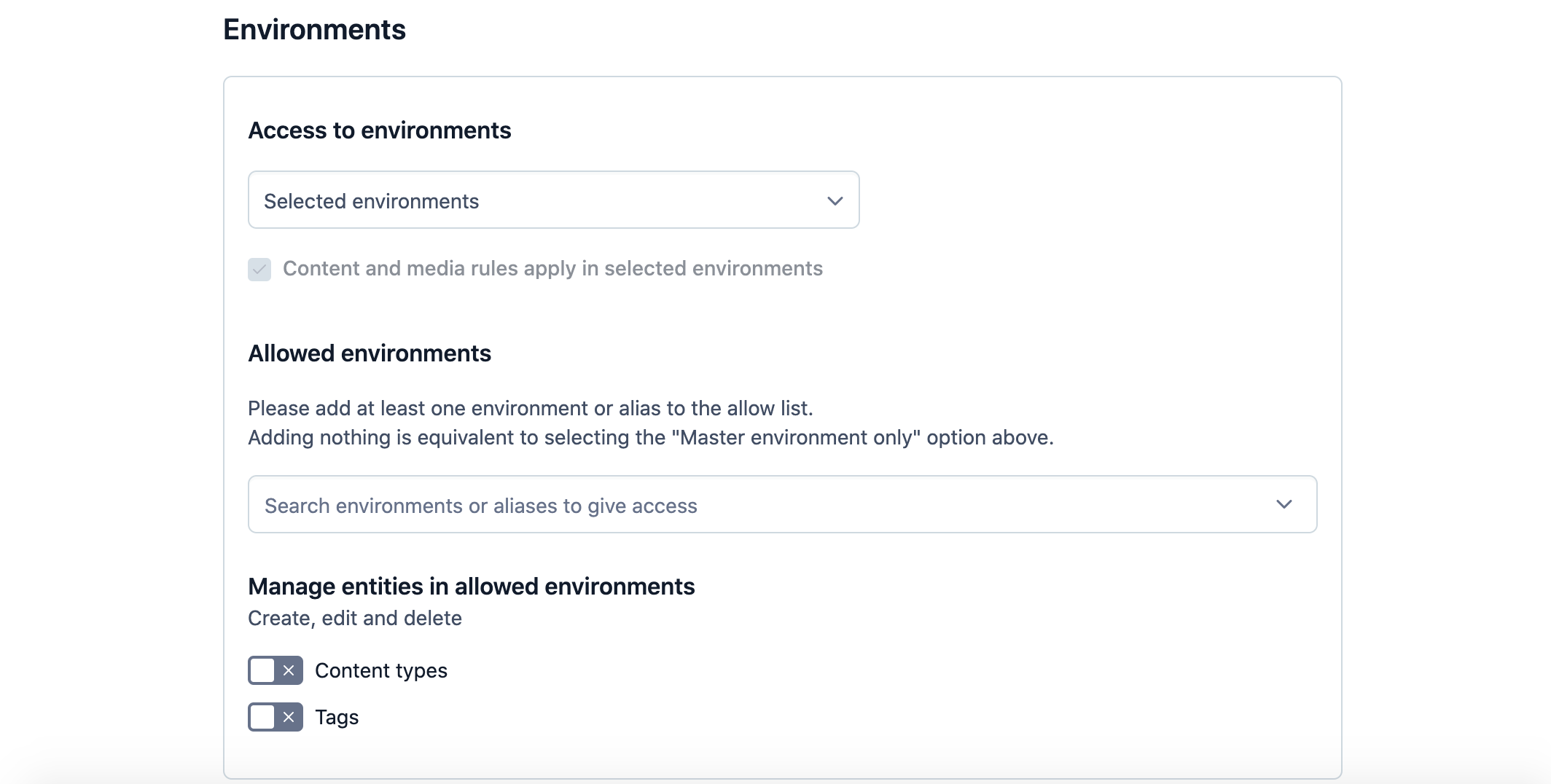
Selected environments - Allows you to select one or multiple specific environments your role will be able to access.
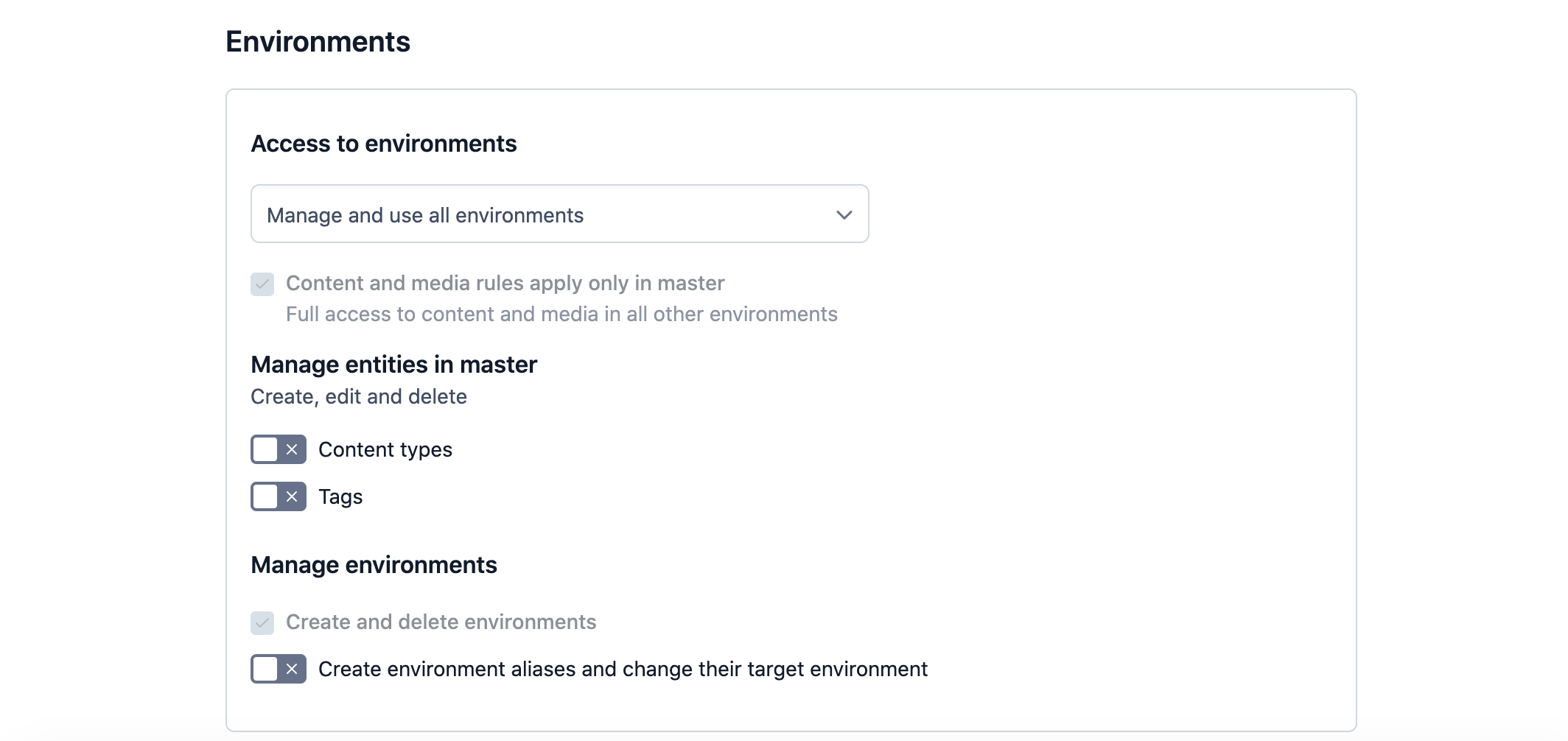
Manage and use all environments - Allows you to set a role to access all environments in a space.
NOTE: With the “Manage and use all environments” permission, the role’s access to master environment content is defined by its content and media permissions. In sandbox environments, this role has full access to all content.
NOTE: A space Administrator role has full access to all environments (including the master environment) and their content.
How to configure access to environments
To configure a role's access to environments:
Go to the Environments tab in the Role editor page.
Under the Access to environments area, select the required environments' access level. If you selected the Selected environments option, please continue to step 3 in How to configure access to a selected environment.
Optional: Under the Manage entities in master/ Manage entities in selected environments area, select the slider(s) to enable the user to create, edit and delete content types and/ or tags.
Optional (only for Manage and use all environments option): Under the Manage environments area, select the slider to enable the user to create environment aliases and change their target environment.
Click Save changes to save the role.
How to configure access to a selected environment
To configure a role's access to a selected environment:
Go to the Environments tab in the Role editor page.
Under the Access to environments area, select the Selected environments option.
Under the Allowed environments area, select the environment you would like your role to be able to access. The environment is added to the Allowed environments list.
Optional: Repeat step 3 to add another environment to the Allowed environments list.
Optional: To remove an environment from the Allowed environments list, click on X button against this environment.
Finish setting environments permissions starting from step 3 in How to configure access to environments.
Assigning multiple environment access options to a single user
When multiple roles are assigned to a single user, the environment access options and related content policies for those roles will be merged. Different environment access options defined in these roles override or combine each other according to the following principles:
“Manage and use all environments” option overrides the “Selected environments” option.
NOTE: The “Manage and use all environments” option is equivalent to setting the Environment permission to “all”. You can read more about this override here. If it is set in any of the roles assigned to a user, this user can access all environments, and any content- or media-related Allow or Deny rule only applies to the master environment. Other environments are fully accessible without restrictions.
“Selected environments” option overrides the “Master environment only” option.
NOTE: The “Selected environments” option needs to explicitly define all environments that a user is allowed to access. A user doesn’t have access to the master environment unless the master environment is added as one of “Allowed environments”.
“Selected environments” options combine to cover all “Allowed environments” across roles.
NOTE: All content- or media-related Allow and Deny rules defined in either of the roles are combined and apply to all environments selected for access in either of the rules. This means that the user has the same content and media restrictions in all selected environments, no matter in which of the roles those rules were defined.
The table and comments below explain how an example combination of roles with different environment permissions assigned to the same user affects the user’s access to environments.
Role A | Role B | Resulting access | |
|---|---|---|---|
User 1 | Environment access: Selected environments: “Staging” environment, “Testing” environment, “POC” environment Content policies: allowed: read all entries denied: edit all entries | Environment access: Manage and use all environments Content policies: allowed: read all assets allowed: edit all entries | Environment access: Manage and use all environments Content policies (apply only in “master”): allowed: read all entries allowed: read all assets denied: edit all entries |
User 2 | Environment access: “Master environment only” Content policies: allowed: read all entries denied: edit all entries | Environment access: Selected environments: “Staging” environment Content policies: allowed: read all assets allowed: edit all entries | Environment access: “Staging” environment Content policies (apply to the “Staging” environment): allowed: read all entries allowed: read all assets denied: edit all entries |
User 3 | Environment access: Selected environments: “Staging” environment, “Testing” environment Content policies: allowed: read all entries denied: edit all entries | Environment access: Selected environments: “QA” environment, “Master” environment Content policies: allowed: read all assets allowed: edit all entries | Environment access: “Staging”, “Testing”, “QA”, “Master” Content policies (apply to all four environments): allowed: read all entries allowed: read all assets denied: edit all entries |
User 1:
Role A - Environments access is set to “Selected environments” and the allowed environments are: “Staging” and “Testing”.
Role B - Environments access is set to “Manage and use all environments”.
Behavior: Access is granted to all environments, because the “Manage and use all environments” option overrides the “Selected environments” option. When the “Manage and use all environments” option is selected, content-related “allow” and “deny” rules only apply to the master environment. All other environments have no restrictions, meaning that all entries and assets can be read, edited, deleted etc.
User 2:
Role A - Environments access is set to “Master environment only”. It allows reading of entries and denies editing of entries.
Role B - Environments access is set to “Selected environments” and the allowed environment is “Staging”. It allows reading of assets and editing of entries.
Behavior: There is one selected environment the user is explicitly allowed to access. But access to the master environment is not explicitly allowed, which would be expected by only looking at Role A. Tip: To grant User 1 access to the master environment, add it as one of the Selected environments. As roles are merged, the denying of entry editing from Role A overrides the allowing of entry editing in Role B. This means that a user who has these two rules assigned will not be able to edit entries.
User 3:
Role A - Environments access is set to “Selected environments” and the allowed environments are: “Staging” and “Testing”. It allows reading of entries and denies editing of entries.
Role B - Environments access is set to “Selected environments” and the allowed environments are: “QA” and “Master”. It allows reading of assets and editing of entries.
Behavior: As roles are merged, the user has access to all four environments “Staging”, “Testing”, “QA” and “Master”, and can read entries and assets. They cannot edit entries in any of the environments, as, like for User 1, the “deny” rule or Role A overrides the “allow” rule of Role B.
NOTE: To learn more about how content and media permissions combine when multiple roles are assigned to a single user, please refer to Assigning multiple roles to a user.